Authenticating via Kerberos with Keycloak and Windows 2008 Active Directory
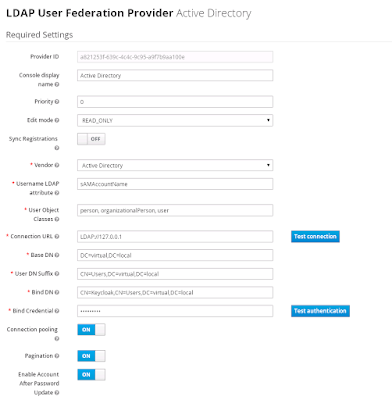
The following instructions show you how to configure Keycloak with Windows AD in order to use Kerberos authentication. Assumptions The Kerberos realm is VIRTUAL.LOCAL The hostname used to access Keycloak is virtual.local. This just means we are running Keycloak on the domain controller. In production virtual.local will be replaced with something like keycloak.dev.virtual.local or something like that, giving you a SPN of HTTP/keycloak.dev.virtual.local@VIRTUAL.LOCAL Configuration Create a windows domain account called Keycloak. Run the following command to assign a SPN to the user and generate a keytab file: ktpass -out keycloak.keytab -princ HTTP/virtual.local@VIRTUAL.LOCAL -mapUser Keycloak@VIRTUAL.LOCAL -pass password1! -kvno 0 -ptype KRB5_NT_PRINCIPAL -crypto RC4-HMAC-NT Verify the SPN has been assigned to the user with the command: setspn -l Keycloak Configure the LDAP settings in Keycloak like this. Since we are running Keycloak on the domain controller, we...