Remember me not - avoiding the Australian metadata dragnet with Tor and Asus
So it is official. As an internet user in the great country of Australia my actions online are now tracked and recorded by the government. And that doesn't sit so well with me.
But rather than complain, I decided to take action and install an Asus RT-N66U router as the gateway on my home network. The router had generally positive reviews online, but I was mostly interested in the fact that it supported third party firmware, like the popular ones provided by a developer calling himself Merlin.
One of the big benefits provided by third party firmware releases is that you get early access to some cool new features. One such feature that caught my eye was the introduction of Tor into the router.
I have used Tor sporadically in the past. While I have to commend the Tor developers for making it easy to install Tor and browse anonymously, the reality is that running an additional piece of software was kind of a pain. It was a mental jump to go from "always online" to "first make sure you have opened the Tor software, wait for it to connect, then go online", especially when the process was different depending on whether you are on a desktop PC or a tablet.
The end result was that I usually spend a few hours on Tor only to eventually put it in the "too inconvenient" basket and give up.
Which is why having Tor enabled at the router level is so nice. It's a one off setup, after which you never have to think about Tor again.
So how well does Tor on the N66U work?
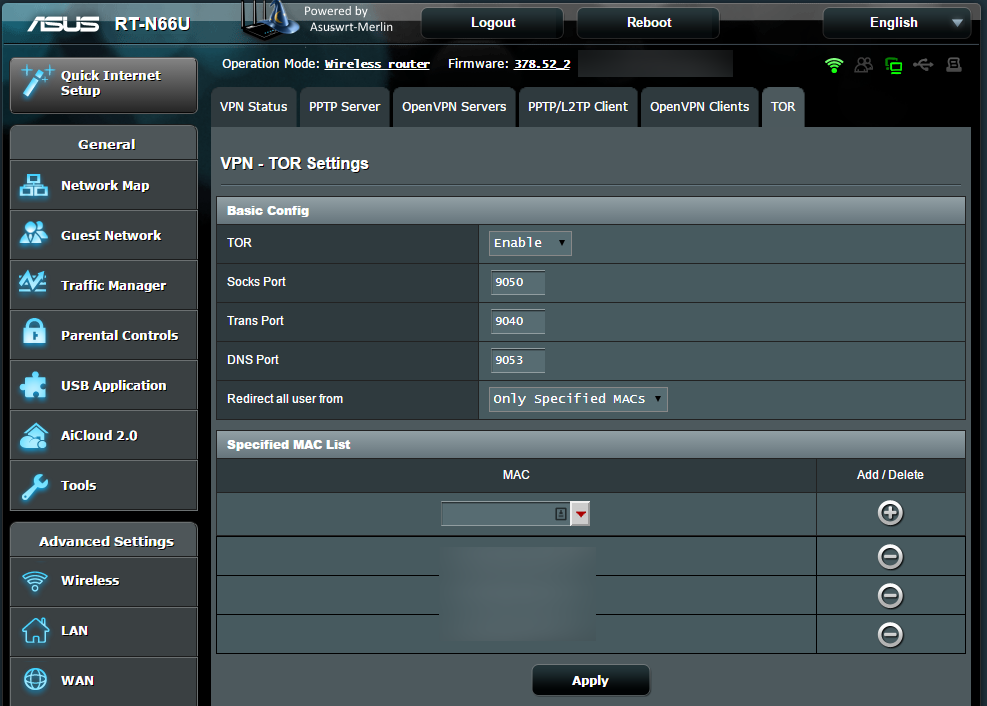
First of all, the configuration is a breeze. Well, a breeze for someone who is knowledgeable enough to be flashing their home router with custom firmware. The process is not going to appeal to those who don't know what a router is, but anyone with a bit of technical knowledge, or a nerdy friend, can be up and running without too much trouble.
As you can see by the screenshot above, enabling Tor is a matter of selecting "Enable" in a drop down list, and deciding on whether to protect the entire network, or just a few select devices.
Once Tor is enabled, there is nothing more that needs to be done on the devices that you have selected. There is no software to be installed, and no process required to enable Tor.
This convenience comes at a cost though. Tor is only as secure as those applications whose data it is transferring, and one of the benefits of the Tor bundle is a browser that has disabled a number of plugins that are known to leak identifiable information.
However, my goal is to frustrate the government metadata dragnet that has been cast over this country's internet rather than achieve anonymity. Now that the average Australian citizen has to treat their ISP as a Man-In-The-Middle attacker, I'm willing to trade a little less anonymity for the convenience of having the packets that make up my web browsing obscured in a way that makes the government's logging efforts mostly meaningless.
Performance wise, there is a noticeable lag as you open web pages, and complex pages (i.e. 90% of the pages you'll view online) take noticeably longer to load. You'll also notice that the browser continues to show pages as still loading long after the page has been displayed to you. This is most likely because background scripts loading analytics and advertising scripts are still being download after the main content of the page has been displayed. Initially it is a little disconcerting to see pages taking so long to completely load, but you quickly learn to ignore the spinning icon on the browser tab and jump in once the page is rendered.
Overall, while this performance lag is noticeable, I never felt that it prevented me from doing what I needed to do online.
The biggest downside to using Tor is the number of Capchas you'll need to fill out to visit every day sites. Google is especially bad, depending on the Tor exit node you happen to be assigned.
But rather than complain, I decided to take action and install an Asus RT-N66U router as the gateway on my home network. The router had generally positive reviews online, but I was mostly interested in the fact that it supported third party firmware, like the popular ones provided by a developer calling himself Merlin.
One of the big benefits provided by third party firmware releases is that you get early access to some cool new features. One such feature that caught my eye was the introduction of Tor into the router.
I have used Tor sporadically in the past. While I have to commend the Tor developers for making it easy to install Tor and browse anonymously, the reality is that running an additional piece of software was kind of a pain. It was a mental jump to go from "always online" to "first make sure you have opened the Tor software, wait for it to connect, then go online", especially when the process was different depending on whether you are on a desktop PC or a tablet.
The end result was that I usually spend a few hours on Tor only to eventually put it in the "too inconvenient" basket and give up.
Which is why having Tor enabled at the router level is so nice. It's a one off setup, after which you never have to think about Tor again.
So how well does Tor on the N66U work?
First of all, the configuration is a breeze. Well, a breeze for someone who is knowledgeable enough to be flashing their home router with custom firmware. The process is not going to appeal to those who don't know what a router is, but anyone with a bit of technical knowledge, or a nerdy friend, can be up and running without too much trouble.
As you can see by the screenshot above, enabling Tor is a matter of selecting "Enable" in a drop down list, and deciding on whether to protect the entire network, or just a few select devices.
Once Tor is enabled, there is nothing more that needs to be done on the devices that you have selected. There is no software to be installed, and no process required to enable Tor.
This convenience comes at a cost though. Tor is only as secure as those applications whose data it is transferring, and one of the benefits of the Tor bundle is a browser that has disabled a number of plugins that are known to leak identifiable information.
However, my goal is to frustrate the government metadata dragnet that has been cast over this country's internet rather than achieve anonymity. Now that the average Australian citizen has to treat their ISP as a Man-In-The-Middle attacker, I'm willing to trade a little less anonymity for the convenience of having the packets that make up my web browsing obscured in a way that makes the government's logging efforts mostly meaningless.
Performance wise, there is a noticeable lag as you open web pages, and complex pages (i.e. 90% of the pages you'll view online) take noticeably longer to load. You'll also notice that the browser continues to show pages as still loading long after the page has been displayed to you. This is most likely because background scripts loading analytics and advertising scripts are still being download after the main content of the page has been displayed. Initially it is a little disconcerting to see pages taking so long to completely load, but you quickly learn to ignore the spinning icon on the browser tab and jump in once the page is rendered.
Overall, while this performance lag is noticeable, I never felt that it prevented me from doing what I needed to do online.
The biggest downside to using Tor is the number of Capchas you'll need to fill out to visit every day sites. Google is especially bad, depending on the Tor exit node you happen to be assigned.
You may find that Google's over zealous bot protection renders the search box on your mobile device useless. Apparently there is no facility on the native Android search widget to prove that you are in fact a human and not a bot scraping Google's search results.
You'll also notice that the ads you are served are now probably in another language. Given that I have clicked on maybe 4 ads in my entire life, this is amusing, and not particularly troublesome.
I even managed to stream videos at 780p. 1080p was asking just a little to much, but if I'm being honest, I don't see much difference between 780p and 1080p anyway.
There are a few things that I didn't try to do over Tor.
The first was streaming Geolocked content (i.e. Netflix). I have a dedicated media PC that uses a VPN (the VPN is also configured through the the N66U) rather than Tor. I imagine that it would be quite difficult to use Tor with something like Netflix, given that you don't have a lot of control as to where your traffic exits the Tor network. One minute you may appear to be in the US, the next in Europe.
I don't torrent, but no one should be using Tor for torrents anyway.
I also don't use applications like Skype. Actually, Skype uses UDP, and won't be routed over Tor anyway.
Even though Tor on the N66U is still in beta, configuration is relatively easy, and I never found myself having to reset the router or perform any kind of troubleshooting. Performance is adequate for day to day browsing, and the ability to only route traffic from specific devices over Tor means that your more bandwidth sensitive devices (like your media PC) are not affected.
Overall, I am quite impressed with how Asus and Merlin have integrated Tor into the N66U. A Tor enabled router is a great way to effortlessly opt out of the Governments metadata dragnet.




Comments
Digital Marketing Course In Hyderabad
Max Estates-360 Gurgaon